While some malware authors will try to create an air of legitimacy around their products to cover themselves from potential criminal cases in the future, one developer of a cryptocurrency stealer isn’t even trying.
According to Palo Alto Networks, malware authors peddling their creations in underground forums will often pretend their products are for educational or research purposes only — a limp attempt to create a legal defense, just in case.
However, a developer making the rounds with a new commodity cryptocurrency stealer has been described as “shameless” by the team.
Indeed, the malware — named WeSteal — is marketed as the “leading way to make money in 2021.”
Palo Alto Networks
Cryptocurrency theft malware, WeSupply Crypto Stealer, has been sold online since May 2020 by a developer under the name WeSupply, and another actor, ComplexCodes, started selling WeSteal in mid-February this year.
An investigation into the sellers, thought to be co-conspirators, has also revealed potential ties to the sale of account access for streaming services including Netflix, Disney+, Doordash, and Hulu.
The team believes that WeSteal is an evolution of the WeSupply Crypto Stealer project. Marketing includes “WeSupply — You profit” and claims that WeSteal is the “world’s most advanced crypto stealer.”
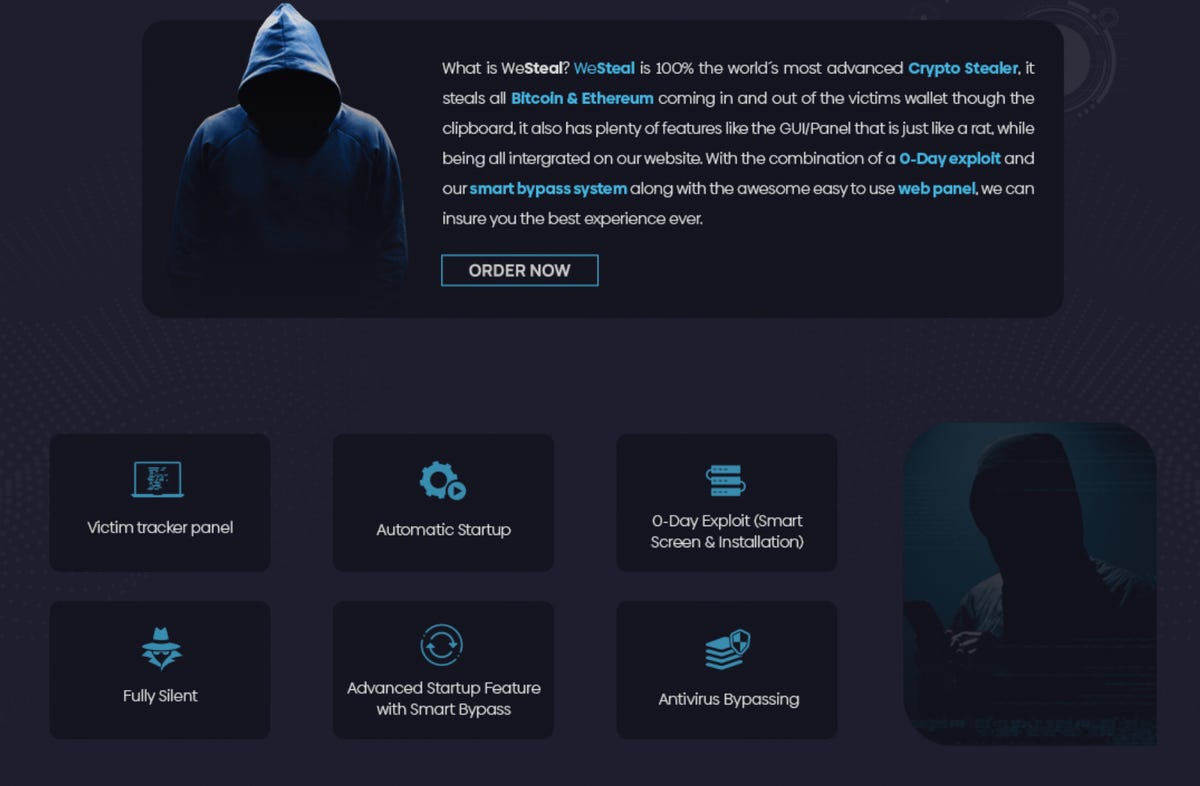
An advertisement for the malware includes features such as a victim tracker panel, automatic start, antivirus software circumvention, and the claim that the malware leverages zero-day exploits.
“It steals all Bitcoin (BTC) and Ethereum (ETH) coming in and out of a victim’s wallet through the clipboard, it also has plenty of features like the GUI/Panel which is just like a RAT [Remote Access Trojan],” the advert reads.
Palo Alto Networks
Litecoin, Bitcoin Cash, and Monero have also been added to the cryptocurrency list.
The researcher’s analysis of the Python-based malware revealed that the malware scans for strings related to wallet identifiers copied to a victim’s clipboard. When these are found, the wallet addresses are replaced with attacker-controlled wallets, which means any transfers of cryptocurrencies end up in the operator’s pocket.
While the malware is also described as having RAT capabilities, the researchers are not convinced, believing that WeSteal has something closer to a simple command-and-control (C2) communication structure rather than containing features usually associated with Trojans — such as keylogging, credential exfiltration, and webcam hijacking.
The WeSteal developers offer C2s as a service and also appear to run some form of customer ‘service’ — however, the current user base appears to be small.
“WeSteal is a shameless piece of commodity malware with a single, illicit function,” the researchers say. “Its simplicity is matched by a likely simple effectiveness in the theft of cryptocurrency. It’s surprising that customers trust their “victims” to the potential control of the malware author, who no doubt could, in turn, usurp them, stealing the victim “bots” or replacing customers’ wallets [..] it’s also surprising the malware author would risk criminal prosecution for what must surely be a small amount of profit.”
A Remote Access Trojan (RAT), WeControl, was also added to the developer’s roster after the report was published and awaits further analysis.
Previous and related coverage
Have a tip? Get in touch securely via WhatsApp | Signal at +447713 025 499, or over at Keybase: charlie0
