- Sysrv is getting updated with additional exploits, targeting a wider spectrum of systems.
- The actors’ goal is to make money at the expense of system resources left vulnerable for years.
- The campaigns have had moderate success thus far, but this could change dramatically soon.
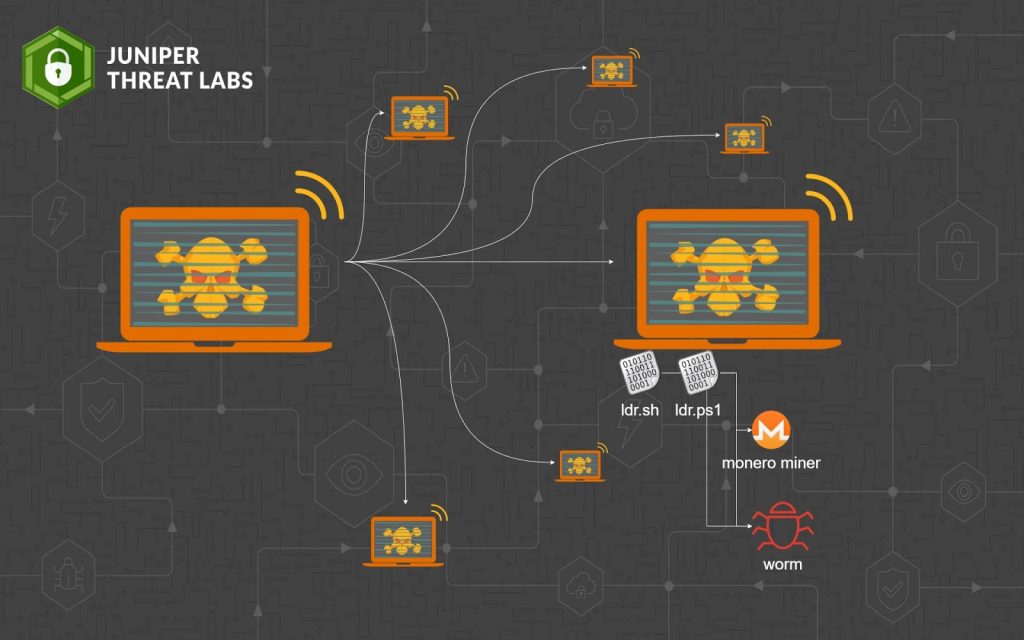
It appears that the authors of the ‘Sysrv’ botnet have been working hard in putting out a more sophisticated version of their malware, as the latest surge in the associated activity is accompanied by expanded capabilities and persistence. The actors’ goal is to install Monero cryptominers and make a profit by burdening the machines of others.
Researchers at Juniper Threat Labs have been following the activity and sampled several iterations of the Sysrv since the start of the year and noticed several changes along the way.
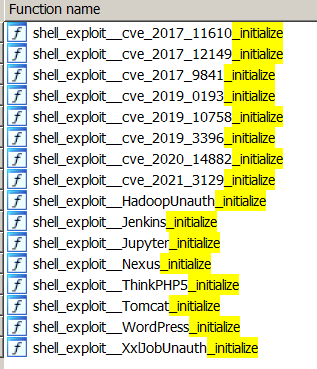
First of all, during the surge of the attacks, the exploits that were hardcoded into Sysrv concerned the following six vulnerabilities:
- Mongo Express RCE (CVE-2019-10758)
- XXL-JOB Unauth RCE
- XML-RPC (CVE-2017-11610)
- CVE-2020-16846 (Saltstack RCE)
- ThinkPHP RCE
- CVE-2018-7600 (Drupal Ajax RCE)
By using these flaws, the actors infect a vulnerable system and use it as a Monero miner as well as a point to help the menace spread further. The worming function relies on random public IP scans using the same list of exploits while the payload is fetched from a hardcoded IP or domain via wget, curl, or PowerShell. The researchers noticed the use of two loader scripts, namely ldr.sh or ldr.sp1.
Sysrv has two binary payloads, one for Linux and one for Windows systems. The miner component is merged with the worm into a single binary in the most recent versions of the malware, whereas previously, it was in the form of a separate binary.
The campaign’s effectiveness seems to be moderate, as the researchers were able to confirm that the actors have made at least a couple of thousand USD on each mining pool since December 2020. By looking into the Shodan search engine’s exploits, it becomes clear that Sysrv was tuned to target systems that have been “abandoned.”
For example, XXL-JOB Unauth RCE is only found in 35 IPs, while the Drupal Ajax RCE (CVE-2018-7600) is now three years old, so there aren’t many systems still vulnerable to it. Even those vulnerable have been exploited by others already, and cryptojackers often take action to prevent subsequent infections from other crooks that could threaten their miners.
However, Sysrv is being actively developed, and its authors are adding more exploits that target recent flaws. The newer versions of the malware include CVE-2021-3129 (Laravel), CVE-2020-14882 (Oracle Weblogic), and CVE-2019-3396 (Widget Connector macro in Atlassian Confluence Server). This alone tells us that Sysrv is here to stay, and it’s going to get nastier with time.