An ongoing malware campaign has been found exploiting recently disclosed vulnerabilities in Linux devices to co-opt the systems into an IRC botnet for launching distributed denial-of-service (DDoS) attacks and mining Monero cryptocurrency.
The attacks involve a new malware variant called “FreakOut” that leverages newly patched flaws in TerraMaster, Laminas Project (formerly Zend Framework), and Liferay Portal, according to Check Point Research’s new analysis published today and shared with The Hacker News.
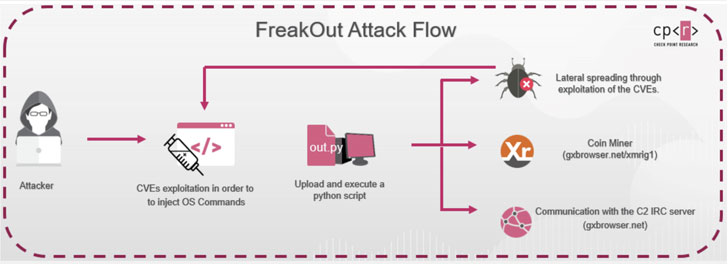
Attributing the malware to be the work of a long-time cybercrime hacker — who goes by the aliases Fl0urite and Freak on HackForums and Pastebin as early as 2015 — the researchers said the flaws — CVE-2020-28188, CVE-2021-3007, and CVE-2020-7961 — were weaponized to inject and execute malicious commands in the server.
Regardless of the vulnerabilities exploited, the end goal of the attacker appears to be to download and execute a Python script named “out.py” using Python 2, which reached end-of-life last year — implying that the threat actor is banking on the possibility that that victim devices have this deprecated version installed.
“The malware, downloaded from the site hxxp://gxbrowser[.]net, is an obfuscated Python script which contains polymorphic code, with the obfuscation changing each time the script is downloaded,” the researchers said, adding the first attack attempting to download the file was observed on January 8.
And indeed, three days later, cybersecurity firm F5 Labs warned of a series of attacks targeting NAS devices from TerraMaster (CVE-2020-28188) and Liferay CMS (CVE-2020-7961) in an attempt to spread N3Cr0m0rPh IRC bot and Monero cryptocurrency miner.
An IRC Botnet is a collection of machines infected with malware that can be controlled remotely via an IRC channel to execute malicious commands.
In FreakOut’s case, the compromised devices are configured to communicate with a hardcoded command-and-control (C2) server from where they receive command messages to execute.
The malware also comes with extensive capabilities that allow it to perform various tasks, including port scanning, information gathering, creation and sending of data packets, network sniffing, and DDoS and flooding.
Furthermore, the hosts can be commandeered as a part of a botnet operation for crypto-mining, spreading laterally across the network, and launching attacks on outside targets while masquerading as the victim company.
With hundreds of devices already infected within days of launching the attack, the researchers warn, FreakOut will ratchet up to higher levels in the near future.
For its part, TerraMaster is expected to patch the vulnerability in version 4.2.07. In the meantime, it’s recommended that users upgrade to Liferay Portal 7.2 CE GA2 (7.2.1) or later and laminas-http 2.14.2 to mitigate the risk associated with the flaws.
“What we have identified is a live and ongoing cyber attack campaign targeting specific Linux users,” said Adi Ikan, head of network cybersecurity Research at Check Point. “The attacker behind this campaign is very experienced in cybercrime and highly dangerous.”
“The fact that some of the vulnerabilities exploited were just published, provides us all a good example for highlighting the significance of securing your network on an ongoing basis with the latest patches and updates.”