Endpoint Security
,
Fraud Management & Cybercrime
,
Fraud Risk Management
Symantec: Attackers Use Weaponized Cobalt Strike to Spread Malware
The Sodinokibi ransomware gang is targeting point-of-sale payment device software after infecting networks with its crypto-locking malware, according to Symantec’s Threat Intelligence team.
See Also: Webinar | 2021: A Cybersecurity Odyssey
While the Symantec researchers found three incidents involving the Sodinokibi gang scanning networks for POS payment software, it’s not clear if the attackers were trying to encrypt the endpoint devices or attempting to scrape vulnerable financial data for resale to other cybercriminals, according to team’s new report.
The latest Sodinokibi campaign started by targeting at least eight organizations using a weaponized version of Cobalt Strike threat emulation software to spread the malware, the report notes. The attackers then infected three of the targeted firms with ransomware and then later scanned their networks for credit card or POS software, the report adds.
So far, this campaign has primarily targeted large, multinational companies in the services, food and healthcare sectors, the report notes.
“The companies were likely targeted because the attackers believed they would be willing to pay a large ransom to recover access to their systems,” the Symantec report notes. “The attackers are aiming to make a lot of money – for victims infected with Sodinokibi, the ransom requested is $50,000 in the monero cryptocurrency if paid within the first three hours and $100,000 after that.”
Because it’s more difficult to trace monero than bitcoin, the Symantec researchers did not determine whether any of the victims paid the ransom demands.
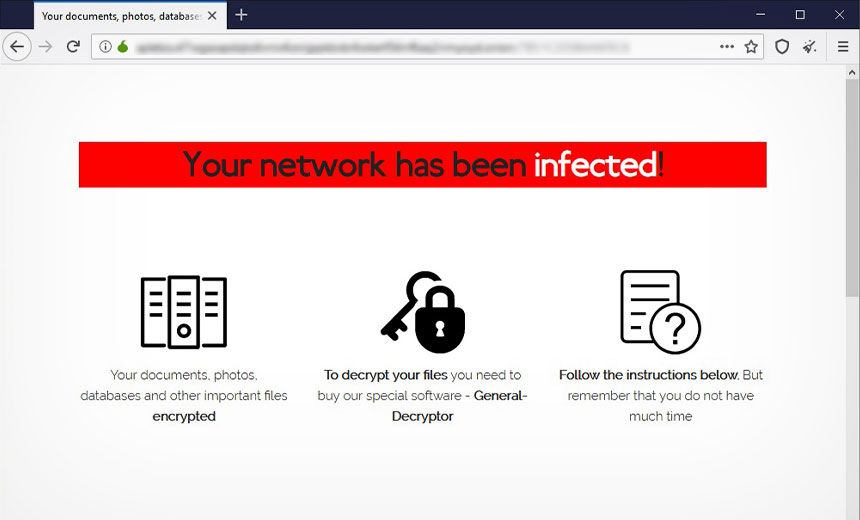
Sodinokibi, also known as REvil and Sodin, has been increasingly focusing on targeting large companies. It’s also offering ransomware as a service to other gangs. In 2019, the gang reaped over than $38 million in ransoms, according to an earlier report from security firm Coveware (see: Ryuk and Sodinokibi Surge as Ransom Payments Double).
Infection Tactics
In the series of attacks that Symantec found, the Sodinokibi gang used several legitimate tools as part of their infection tactics. These include a remote administration client tool created by NetSupport for installing malicious components, a weaponized version of Cobalt Strike to spread malware, Pastebin for hosting the malware and Amazon’s CloudFront service for its command-and-control infrastructure, the report notes.
To infect the victims, the attackers exploited vulnerable network devices or relied on brute-force attacks on remote desktop protocol servers, the Symantec researchers discovered. Once a device was infected, the attackers attempted to evade detection by disabling any security software.
“The attackers also appear to be interested in stealing credentials on victim machines, and are observed adding user accounts, presumably in an attempt to maintain persistence on victim machines and also in a further attempt to keep a low profile on victim network,” the Symantec researchers report.
POS Scanning
In three cases, the gang also scanned for POS or credit card software after infecting the networks with the ransomware, the report notes.
While two of the victims were larger organizations, the attackers scanned the third firm – a somewhat smaller healthcare entity – to determine if the victim was in a position to pay the ransom, the report notes.
Commenting on the POS attacks, the report notes: “One thing that is clear is the actors using Sodinokibi are sophisticated and skilled and show no sign that their activity is likely to decrease anytime soon. It will be interesting to see if this was just opportunistic activity in this campaign, or if it is set to be a new tactic adopted by targeted ransomware gangs.”
Other security researchers took note of this development as well.
Interesting development with Sodinokibi #ransomware “campaign in which the attackers are also scanning the networks of some victims for credit card or point of sale (PoS) software” via @threatintel https://t.co/7fFzhMe0KH #malware #cybercrime pic.twitter.com/EczpQpHDyn
— Raj Samani (@Raj_Samani) June 24, 2020
History of Attacks
Sodinokibi was first spotted in around June 2019 after the administrators of GrandCrab, a ransomware-as-a-service criminal group, announced its closure. Security experts believe that the operators of GandCrab are likely behind Sodiokibi.
In April, the London-based foreign currency exchange firm Travelex paid a ransom of $2.3 million to regain access to its data after Sodinokibi attacked its systems (see: Travelex Paid $2.3 Million to Ransomware Gang: Report).
In May, the Sodinokibi gang began pressuring a high-profile New York law firm to pay a $42 million ransom, threatening to release more data on the firm’s roster of celebrity clients following a ransomware attack (see: Ransomware Gangs Go (Lady) Gaga for Data Breaches).
