COVID-19
,
Endpoint Detection & Response (EDR)
,
Endpoint Security
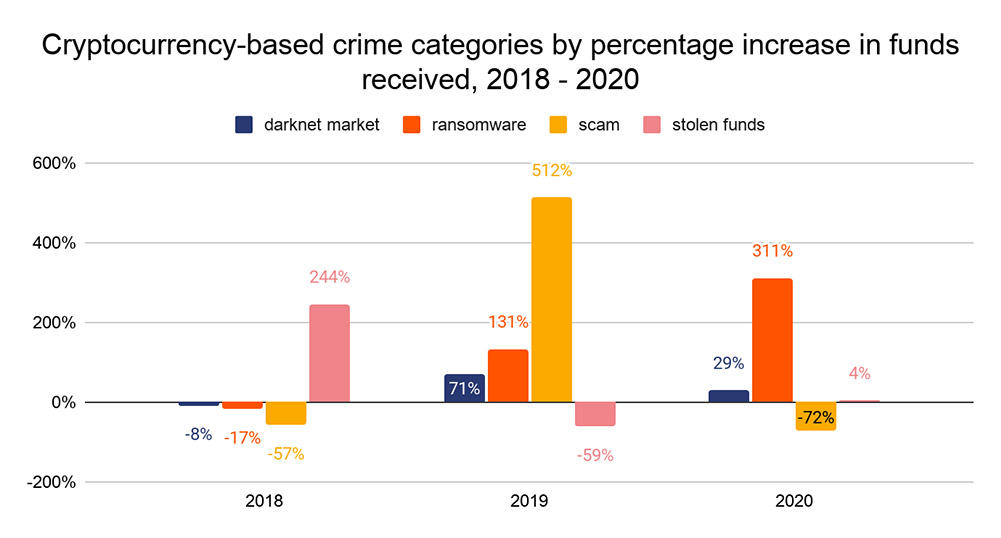
Unfortunately, Ransomware Profits Surged by 311% From 2019, Chainalysis Reports
Ransomware now dominates the cybercrime landscape, and one measure of its continuing success has been the surge in funds flowing to criminal-controlled cryptocurrency wallets.
See Also: Top 50 Security Threats
Even so, here’s some good news on the cybercrime front: “Cryptocurrency-related crime fell significantly in 2020,” reports blockchain analysis firm Chainalysis.
That’s despite the value of bitcoin surging past $28,000 by the end of 2020, ahead of hitting a record high above $40,000 in early January.
“In 2019, criminal activity represented 2.1% of all cryptocurrency transaction volume, or roughly $21.4 billion worth of transfers,” Chainalysis reports. “In 2020, the criminal share of all cryptocurrency activity fell to just 0.34%, or $10 billion in transaction volume.”
What’s behind the drop in criminal activity as a percentage of all cryptocurrency transactions? One reason is because more noncriminals have been using bitcoin. “Overall, economic activity nearly tripled between 2019 and 2020,” Chainalysis reports. In addition, the overall volume of scams declined, it found.
Ransomware Profits Increase 311%
Unfortunately, crime tied to darknet markets increased from 2019 to 2020, while ransomware profits surged. “Ransomware accounted for just 7% of all funds received by criminal addresses, at just under $350 million worth of cryptocurrency,” Chainalysis reports. “But that figure represents a 311% increase over 2019. No other category of cryptocurrency-based crime rose so dramatically in 2020.”
One ransomware driver may have been the massive switch to remote working, with criminals seeking to exploit potential vulnerabilities in enterprise infrastructure due to the COVID-19 pandemic, it adds.
The ransomware problem is also likely much worse than researchers can currently calculate. Experts say that unless ransomware results in the exposure of personal data, thus triggering data breach notification rules, many ransomware incidents – and payoffs – never get publicly reported.
“Ransomware estimates should always be considered lower bounds due to underreporting, and … the 2020 figure for total ransomware payments will likely grow as we identify more addresses associated with different strains, particularly in the later months of the year,” Chainalysis says.
Security researchers Brian Carter and Vitali Kremez, for example, recently identified 61 bitcoin addresses used by the Ryuk ransomware operators and affiliates. They found that their wallets held more than $150 million.
Another example: Chainalysis previously reported that criminal activity in 2019 had represented just 1.1% of all cryptocurrency transaction volume. Since then, however, it’s identified more wallets tied to criminal activity, leading it to update the figure to 2.2%.
Why Criminals Still Love Cryptocurrency
While the total cryptocurrency funds received by illicit entities declined in 2020, Chainalysis reports, criminals continue to love cryptocurrency – with bitcoin still dominating – because using pseudonymizing digital currencies gives them a way to easily receive funds from victims. Cryptocurrency also supports darknet market transactions, with many markets offering escrow services to help protect buyers and sellers against fraud.
Using cryptocurrency, criminals can access a variety of products and services, such as copies of malware or hacking tools, complete sets of credit card details known as fullz, and tumbling or mixing services provided by a third-party service or technology that will launder bitcoins by attempting to mix them by routing them between numerous addresses. Criminals have also been using a legitimate concept called “coinjoin,” which is sometimes built into cryptocurrency wallets as a feature. It allows users to mix virtual coins together while paying for separate transactions, which can complicate attempts to trace any individual transactions.
Intelligence and law enforcement agencies have some closely held ability to correlate the cashing out of cryptocurrency with deposits that get made into individuals’ bank accounts. But whatever insights they might have, it hasn’t been enough to track down and charge all cryptocurrency-using criminals, many of whom live in jurisdictions, such a Russia, that western governments can’t reach.
In the meantime, ransomware-wielding extortionists have been running increasingly sophisticated operations. One measure of that is in the level of sophistication wielded by groups such as Sodinokibi, aka REvil.
“One of the most prolific groups right now, the REvil ransomware gang, they have actually had an insider who’s gone out to media and flipped on some of their operations and basically been telling how they operate,” says Greg Foss, a senior cybersecurity strategist at VMware. “That’s how we’ve learned more about how their revenue is structured and how many people make up these organizations.”
REvil and other groups, including the now-defunct Maze – which appears to have spun off Egregor and may have close ties to the Russian government – have been increasingly hiring specialists across numerous areas, ranging from network penetration and encryption to negotiations and working with cloud-based data.
Time to Ban Ransom Payoffs?
Governments haven’t been sitting still. Regulators in some countries, for example, have been driving cryptocurrency exchanges to improve their reporting and compliance with anti-money laundering laws. Law enforcement agencies have also been cracking down on mixing sites, darknet markets and more.
Some experts, however, say much more must be done. Ciaran Martin, who until last August served as the CEO of the U.K.’s National Cyber Security Center, the public-facing arm of intelligence agency GCHQ, argues that ransom payments might need to be banned outright or at least much more heavily regulated.
In Britain, as in other countries, paying a ransom – except to terrorists – is typically not illegal. But Martin tells The Guardian that one regret from his time serving as Britain’s cybersecurity chief is not getting laws updated to better regulate payments to extortionists, especially as ransomware profits have boomed. So, he’s calling for an urgent legal review, including of the insurance sector, because so much cybercrime profit is being funded by victims’ cyber insurance payouts.
“In the last year, experts are saying this is close to getting out of control,” Martin says. “The law is nobody’s fault; it was written for another purpose, but it has become OK to pay out to criminals”.
